Introduction
The Tor Project web site makes a bold claim to its users:
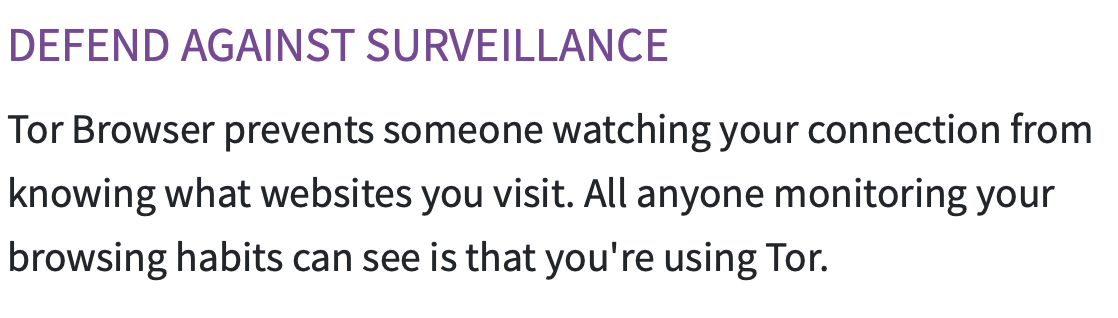
Don't misinterpret this claim. It's not true that Tor protects you against "anyone monitoring your browsing".
On this web page, I provide you with the critical information missing from the Tor Project's website: if you estimate your adversary's resources in dollars, I'll estimated the probability that Tor will fail to protect you.
Risk Calculator
The first step in determining if Tor is secure is to ask yourself, How much money does my adversary have? Use this slider to indicate the adversary's total monthly budget for all targets. In other words, the total budget your adversary has to spend on you and anyone else using Tor. Then pick one of three scenarios.
Adversary's goal: determine the IP address of an onion service server. The chances that the adversary will defeat Tor's protections and determine your onion server's real IP address with the most basic approach are as follows.
Loading...
Adversary's goal: determine your IP address as a visitor to a secure drop site, as offered by some newspapers to whistleblowers. Use the slider to indicate how many times the whistleblower visits the SecureDrop site. For example, if they upload a document and then return later to view a newspaper's response, that is 2 visits.
Loading...
Adversary's goal: determine both your own home IP address and the clear web sites you are visiting with Tor Browser. In this calculation, assume you have been using Tor Browser for the past month. Use the slider to indicate how many hours a week you have used Tor Browser in this example scenario.
[Loading...]
Even low-resource adversaries of journalists and dissidents are not blocked by Tor. It's unethical that the Tor Project advertises their software as providing protection without being specific about who is protected by Tor. In fact, it's unethical according to their own standards:
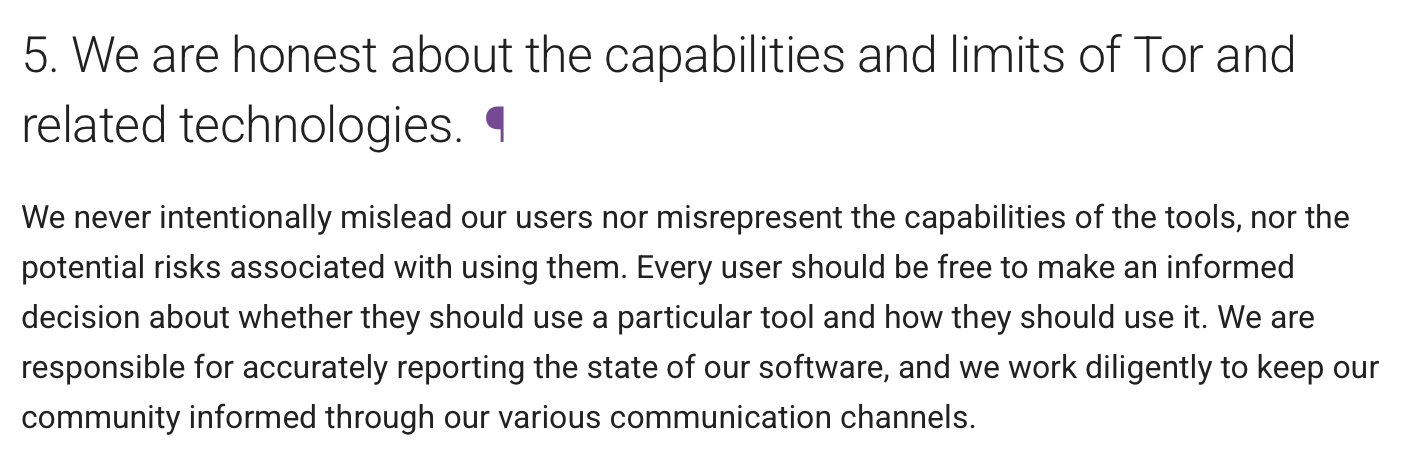 Why has the Tor Project maintained a network that has been used extensively for child sexual abuse for decades when it doesn't offer much protection for the groups it aims to protect? The Tor Project is a lose-lose outcome. Since 2017, the Canadian Centre for Child Protection (C3P) has identified: 44,336 unique onion services that have directly hosted child sexual abuse material (CSAM); and 2,853,485 CSAM images or videos that have been directly hosted on Onion services. As C3P will tell you: CSAM distribution on Tor onion services is not inevitable. The small set of people that centrally control Tor software and centrally manage the Tor network have the power to act to stop this abuse without lessening their (weak) protections.
Why has the Tor Project maintained a network that has been used extensively for child sexual abuse for decades when it doesn't offer much protection for the groups it aims to protect? The Tor Project is a lose-lose outcome. Since 2017, the Canadian Centre for Child Protection (C3P) has identified: 44,336 unique onion services that have directly hosted child sexual abuse material (CSAM); and 2,853,485 CSAM images or videos that have been directly hosted on Onion services. As C3P will tell you: CSAM distribution on Tor onion services is not inevitable. The small set of people that centrally control Tor software and centrally manage the Tor network have the power to act to stop this abuse without lessening their (weak) protections.
Frequently Asked Questions
What does it mean to be "secure"?
Here is my preferred definition of what it means to be secure.
Information is secure if it costs more to gain access to the information than the information is worth to the adversary.
For example, let's say I store $100 in a safe. My money is secure if it costs at least $100 to buy a good drill that can crack open the safe.
The world's standards for encrypting data are so secure that no one has enough money or time to brute force their way into properly encrypted data, not even governments. They are better off waiting for a scientific breakthrough that may never come.
Does Tor offer the same level of security for its users as these encryption standards? Not even close. One needs very little time and money to defeat Tor's mechanisms for securing its users' IP addresses.
How much do you assume each relay costs per month?
When you load this page, the default is $25/month based on some web searches I made. Do you disagree? Then please adjust that value to anything you wish using this input box:What is required of an adversary given Tor's protections?
When you use Tor, your traffic is relayed through a series of computers running Tor. Each relay represents an opportunity for an adversary to observe traffic. I have assumed adversaries cannot break Tor's encryption in my calculations. Tor's weak point is well known to be the randomness of relay selection. Who is authorized to run a relay? Everyone in the world is authorized to run a relay, including your adversary. The Tor Project website explains this in hard-to-understand language:
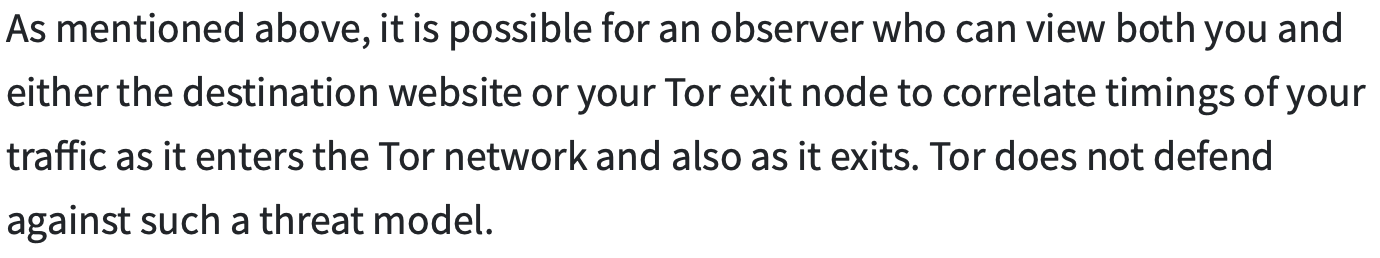
Do you think Tor users can make an "informed decision" from that sentence? Do they know who exactly can do that? The answer is anyone who has the money to do it. Do you think Tor users know how much money that is?
How did you calculate these values?
Every ten minutes or so while using Tor, your relays change and an adversary gains another chance to observe and correlate traffic. (Tor changes paths about every ten minutes.)
When you use Tor, your communications travel through a series of these computer relays running the Tor software. The relay computers that are closest to you, the user, in the chain are called guards. The computer relays closest to the destination website are called exits.
Each relay that an adversary operates is like a raffle ticket for a lottery where the prize is determining your computer's IP address. (Once your adversary knows your IP address, in most cases, they can likely find your internet service provider and from there, perhaps your street address.) The more tickets your adversary has, the better chance they have of winning the lottery. Each relay costs your adversary money.
On the other hand, the more relays running that are not operated by your adversary, the harder it is for the adversary to win.
How many relays are running worldwide? I've retrieved this information from the Tor Project's web site and I use it as the basis of the values I show. I'll update these values occasionally.
Current Guard relays: [Loading...]
Current Exit relays: [Loading...]
What's the math behind these calculations?
If my explanation in the prior question is not detailed enough for you, you can read about the math I used in these estimates here.
Is this new information?
This information is not new (e.g., see this 2006 paper). I have been teaching these concepts in my college course for years; there is no big reveal here. The Tor Project simply has not put together this information for its users. I asked them directly to do in 2019.
If Tor Onion services are so weak, then why is it a problem to rescue children from sexual exploitation?
It takes time for investigators to act. Even if they are eventually successful, in the meantime, a lot of harms have taken place on Tor Onion sites, including:
- Users have been able to distribute CSAM to each other.
- Perpetrators have had a chance to normalize crimes against children to one another.
- Perpetrators have had a chance to train each other on how to groom children.
- Perpetrators have had a chance to train each other other on how to evade detection.
And at the same time, the Tor Project is not offering reasonable protection to people acting ethically who deserve privacy. Ethical users of Tor are owed an honest and clear message from the Tor Project about what level of protection is provided. To be clear, I very much believe people deserve privacy — I am a privacy researcher. For me, "people" includes children.
Why should I trust your results?
I have worked as a researcher and professor in this field for more than two decades. But you do not have to trust my results; you can verify them yourself. You can check my math here, and I have provided the source code for the calculations here. If you find any errors, you can let me know with this google form and if I agree, I'd be happy to fix them. I am providing a simple model, and I wish for this page to open a discussion and not to end one.Conclusion
Is Tor secure? Ask: who is your adversary and how much money are they willing to spend on you and people like you? If you are a dissident or journalist, I think your adversary has enough money to get around Tor's hurdles. It's unethical that the Tor Project advertises its software as protective of journalists and dissidents.
Things are much worse than I'm indicating on this web page. There are many other ways to gain access to your real IP address and reveal your identity. Just because someone doesn't have the budget to break Tor's protections does not mean there isn't another way to get your identity.